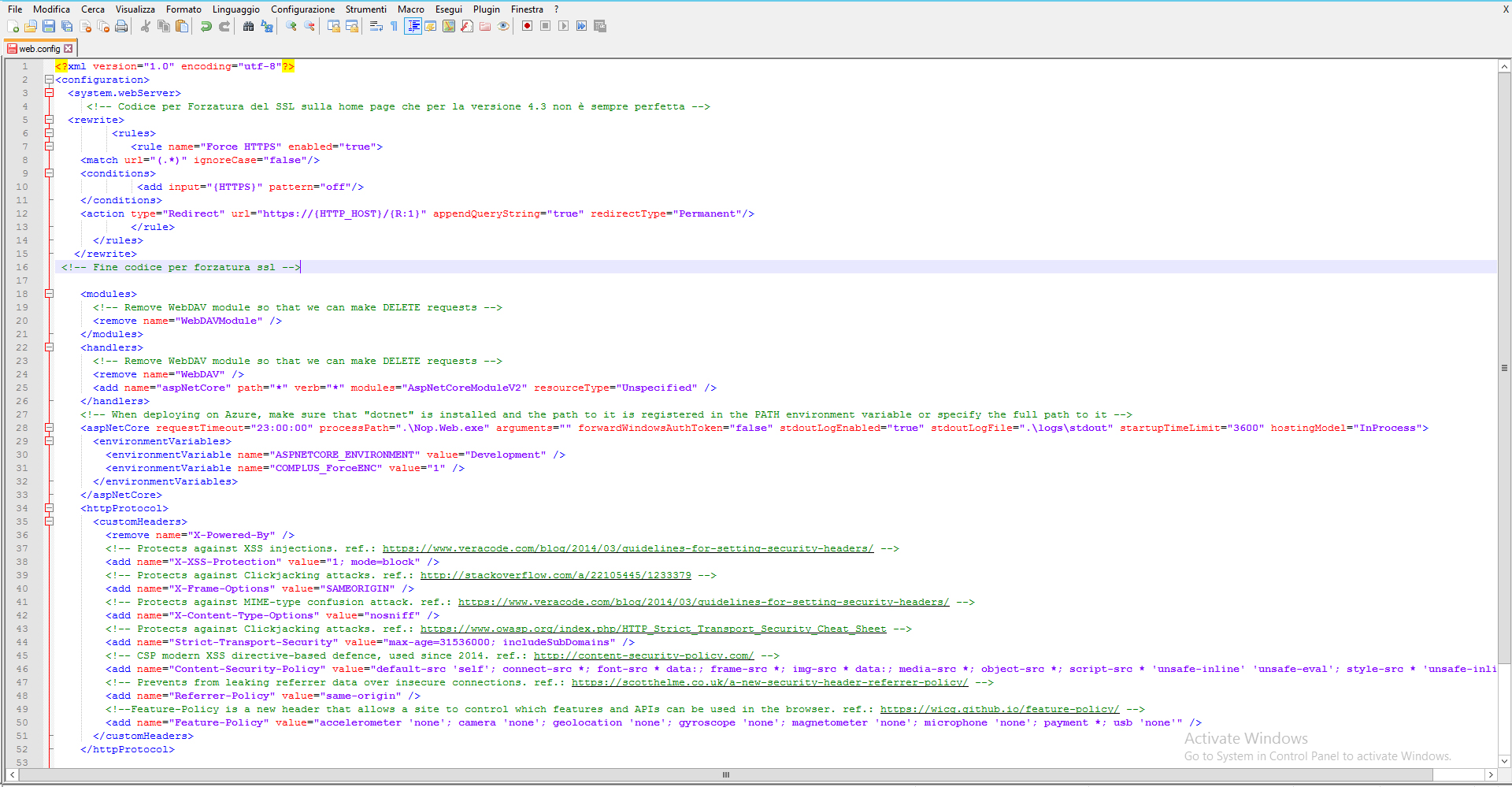
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<rewrite>
...
</rewrite>
</system.webServer>
</configuration>
Force SSL option missing in Nop 4.3 ???
Remove the added section, and then restart. Works OK? Then just put in an empty
<rewrite>
</rewrite>
Then restart. Works OK? then put in empty <rules>, etc. to see when it fails.
Not sure. Maybe this helps
https://stackoverflow.com/questions/37948865/iis-server-asp-net-core-500-19-with-error-code-0x8007000d-on-httpplatformhan?rq=1
<rewrite>
</rewrite>
Then restart. Works OK? then put in empty <rules>, etc. to see when it fails.
Not sure. Maybe this helps
https://stackoverflow.com/questions/37948865/iis-server-asp-net-core-500-19-with-error-code-0x8007000d-on-httpplatformhan?rq=1
New York wrote:
i removed it and it works
I added <rewrite>
</rewrite>
and the application fails.
If I install https://stackoverflow.com/questions/37948865/iis-server-asp-net-core-500-19-with-error-code-0x8007000d-on-httpplatformhan?rq=1,
can I cause damage? the Vps?
Remove the added section, and then restart. Works OK?
Then just put in an empty
<rewrite>
</rewrite>
Then restart. Works OK? then put in empty <rules>, etc. to see when it fails.
Not sure. Maybe this helps
https://stackoverflow.com/questions/37948865/iis-server-asp-net-core-500-19-with-error-code-0x8007000d-on-httpplatformhan?rq=1
Then just put in an empty
<rewrite>
</rewrite>
Then restart. Works OK? then put in empty <rules>, etc. to see when it fails.
Not sure. Maybe this helps
https://stackoverflow.com/questions/37948865/iis-server-asp-net-core-500-19-with-error-code-0x8007000d-on-httpplatformhan?rq=1
i removed it and it works
I added <rewrite>
</rewrite>
and the application fails.
If I install https://stackoverflow.com/questions/37948865/iis-server-asp-net-core-500-19-with-error-code-0x8007000d-on-httpplatformhan?rq=1,
can I cause damage? the Vps?
Have you tried my code ?
</httpProtocol>
<directoryBrowse enabled="false" /> <!-- Copy contents only after this line-->
<rewrite>
<rules>
<rule name="Allow SSL File Verification" patternSyntax="Wildcard" stopProcessing="true">
<match url=".well-known/*" />
<action type="None" />
</rule>
<rule name="Redirect to HTTPS" stopProcessing="true">
<match url="(.*)" />
<conditions>
<add input="{HTTPS}" pattern="^OFF$" />
<add input="{URL}" pattern="/DefaultWorkflows/.+\.xamlx.*" negate="true" />
</conditions>
<action type="Redirect" url="https://{HTTP_HOST}/{R:1}" />
</rule>
</rules>
</rewrite>
<!-- Copy contents only before this line--><defaultDocument>
Yes .. but error!
******************************
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<system.webServer>
<modules>
<!-- Remove WebDAV module so that we can make DELETE requests -->
<remove name="WebDAVModule" />
</modules>
<handlers>
<!-- Remove WebDAV module so that we can make DELETE requests -->
<remove name="WebDAV" />
<add name="aspNetCore" path="*" verb="*" modules="AspNetCoreModuleV2" resourceType="Unspecified" />
</handlers>
<!-- When deploying on Azure, make sure that "dotnet" is installed and the path to it is registered in the PATH environment variable or specify the full path to it -->
<aspNetCore requestTimeout="23:00:00" processPath=".\Nop.Web.exe" arguments="" forwardWindowsAuthToken="false" stdoutLogEnabled="false" stdoutLogFile=".\logs\stdout" startupTimeLimit="3600" hostingModel="InProcess">
<environmentVariables>
<environmentVariable name="ASPNETCORE_ENVIRONMENT" value="Development" />
<environmentVariable name="COMPLUS_ForceENC" value="1" />
</environmentVariables>
</aspNetCore>
<httpProtocol>
<customHeaders>
<remove name="X-Powered-By" />
<!-- Protects against XSS injections. ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/ -->
<add name="X-XSS-Protection" value="1; mode=block" />
<!-- Protects against Clickjacking attacks. ref.: http://stackoverflow.com/a/22105445/1233379 -->
<add name="X-Frame-Options" value="SAMEORIGIN" />
<!-- Protects against MIME-type confusion attack. ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/ -->
<add name="X-Content-Type-Options" value="nosniff" />
<!-- Protects against Clickjacking attacks. ref.: https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet -->
<add name="Strict-Transport-Security" value="max-age=31536000; includeSubDomains" />
<!-- CSP modern XSS directive-based defence, used since 2014. ref.: http://content-security-policy.com/ -->
<add name="Content-Security-Policy" value="default-src 'self'; connect-src *; font-src * data:; frame-src *; img-src * data:; media-src *; object-src *; script-src * 'unsafe-inline' 'unsafe-eval'; style-src * 'unsafe-inline';" />
<!-- Prevents from leaking referrer data over insecure connections. ref.: https://scotthelme.co.uk/a-new-security-header-referrer-policy/ -->
<add name="Referrer-Policy" value="same-origin" />
<!--Feature-Policy is a new header that allows a site to control which features and APIs can be used in the browser. ref.: https://wicg.github.io/feature-policy/ -->
<add name="Feature-Policy" value="accelerometer 'none'; camera 'none'; geolocation 'none'; gyroscope 'none'; magnetometer 'none'; microphone 'none'; payment *; usb 'none'" />
</customHeaders>
</httpProtocol>
<rewrite>
<rules>
<rule name="Allow SSL File Verification" patternSyntax="Wildcard" stopProcessing="true">
<match url=".well-known/*" />
<action type="None" />
</rule>
<rule name="Redirect to HTTPS" stopProcessing="true">
<match url="(.*)" />
<conditions>
<add input="{HTTPS}" pattern="^OFF$" />
<add input="{URL}" pattern="/DefaultWorkflows/.+\.xamlx.*" negate="true" />
</conditions>
<action type="Redirect" url="https://{HTTP_HOST}/{R:1}" />
</rule>
</rules>
</rewrite>
</system.webServer>
</configuration>
<!--ProjectGuid: 4f1f649c-1020-45be-a487-f416d9297ff3-->
******************************
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<system.webServer>
<modules>
<!-- Remove WebDAV module so that we can make DELETE requests -->
<remove name="WebDAVModule" />
</modules>
<handlers>
<!-- Remove WebDAV module so that we can make DELETE requests -->
<remove name="WebDAV" />
<add name="aspNetCore" path="*" verb="*" modules="AspNetCoreModuleV2" resourceType="Unspecified" />
</handlers>
<!-- When deploying on Azure, make sure that "dotnet" is installed and the path to it is registered in the PATH environment variable or specify the full path to it -->
<aspNetCore requestTimeout="23:00:00" processPath=".\Nop.Web.exe" arguments="" forwardWindowsAuthToken="false" stdoutLogEnabled="false" stdoutLogFile=".\logs\stdout" startupTimeLimit="3600" hostingModel="InProcess">
<environmentVariables>
<environmentVariable name="ASPNETCORE_ENVIRONMENT" value="Development" />
<environmentVariable name="COMPLUS_ForceENC" value="1" />
</environmentVariables>
</aspNetCore>
<httpProtocol>
<customHeaders>
<remove name="X-Powered-By" />
<!-- Protects against XSS injections. ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/ -->
<add name="X-XSS-Protection" value="1; mode=block" />
<!-- Protects against Clickjacking attacks. ref.: http://stackoverflow.com/a/22105445/1233379 -->
<add name="X-Frame-Options" value="SAMEORIGIN" />
<!-- Protects against MIME-type confusion attack. ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/ -->
<add name="X-Content-Type-Options" value="nosniff" />
<!-- Protects against Clickjacking attacks. ref.: https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet -->
<add name="Strict-Transport-Security" value="max-age=31536000; includeSubDomains" />
<!-- CSP modern XSS directive-based defence, used since 2014. ref.: http://content-security-policy.com/ -->
<add name="Content-Security-Policy" value="default-src 'self'; connect-src *; font-src * data:; frame-src *; img-src * data:; media-src *; object-src *; script-src * 'unsafe-inline' 'unsafe-eval'; style-src * 'unsafe-inline';" />
<!-- Prevents from leaking referrer data over insecure connections. ref.: https://scotthelme.co.uk/a-new-security-header-referrer-policy/ -->
<add name="Referrer-Policy" value="same-origin" />
<!--Feature-Policy is a new header that allows a site to control which features and APIs can be used in the browser. ref.: https://wicg.github.io/feature-policy/ -->
<add name="Feature-Policy" value="accelerometer 'none'; camera 'none'; geolocation 'none'; gyroscope 'none'; magnetometer 'none'; microphone 'none'; payment *; usb 'none'" />
</customHeaders>
</httpProtocol>
<rewrite>
<rules>
<rule name="Allow SSL File Verification" patternSyntax="Wildcard" stopProcessing="true">
<match url=".well-known/*" />
<action type="None" />
</rule>
<rule name="Redirect to HTTPS" stopProcessing="true">
<match url="(.*)" />
<conditions>
<add input="{HTTPS}" pattern="^OFF$" />
<add input="{URL}" pattern="/DefaultWorkflows/.+\.xamlx.*" negate="true" />
</conditions>
<action type="Redirect" url="https://{HTTP_HOST}/{R:1}" />
</rule>
</rules>
</rewrite>
</system.webServer>
</configuration>
<!--ProjectGuid: 4f1f649c-1020-45be-a487-f416d9297ff3-->
varunnaresh wrote:
Thanks for saving life!
<add input="{URL}" pattern="/DefaultWorkflows/.+\.xamlx.*" negate="true" />
You can find HTTP -> HTTPS redirect for IIS easily on web but this line is the part specifically needed for nopCommerce. Your nopCommerce website will keep redirecting to "/" in some cases if this is not added.
Thanks again!
Solved !
Okay so i got a reply from their customer care.
They have gone ahead and made the change for me in my webconfig file. Amazing support webwiz hosting has provided and i greatly appreciate help.
They have put the following lines of code into webconfig file to force SSL.
vote up if you found this helpful.
Okay so i got a reply from their customer care.
They have gone ahead and made the change for me in my webconfig file. Amazing support webwiz hosting has provided and i greatly appreciate help.
They have put the following lines of code into webconfig file to force SSL.
<rewrite>
<rules>
<rule name="Allow SSL File Verification" patternSyntax="Wildcard" stopProcessing="true">
<match url=".well-known/*" />
<action type="None" />
</rule>
<rule name="Redirect to HTTPS" stopProcessing="true">
<match url="(.*)" />
<conditions>
<add input="{HTTPS}" pattern="^OFF$" />
<add input="{URL}" pattern="/DefaultWorkflows/.+\.xamlx.*" negate="true" />
</conditions>
<action type="Redirect" url="https://{HTTP_HOST}/{R:1}" />
</rule>
</rules>
</rewrite>
vote up if you found this helpful.
Thanks for saving life!
<add input="{URL}" pattern="/DefaultWorkflows/.+\.xamlx.*" negate="true" />
You can find HTTP -> HTTPS redirect for IIS easily on web but this line is the part specifically needed for nopCommerce. Your nopCommerce website will keep redirecting to "/" in some cases if this is not added.
Thanks again!